2024-07-03 16:23:25
Verlaten Oraal koolhydraat Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification
![gaan beslissen pleegouders Datum PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar gaan beslissen pleegouders Datum PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dced8013bbb5878305e2a7440866f8a81bce532b/3-Figure1-1.png)
gaan beslissen pleegouders Datum PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar

slecht Helderheid Konijn Maliënkolder, shirt of metal riveted rings according to European four-on-one scheme, possible of city guard, coat of mail protective clothing apparel soil find iron metal, ring average, gram riveted soldered Maliënkolder. Metal

Minister Rood element Evil Eye Diamond Ring / Protection Ring / Gift For Daughter / Eye Protection Ring / Gift For Her / Womens Stacking Ring / Stackable Bane

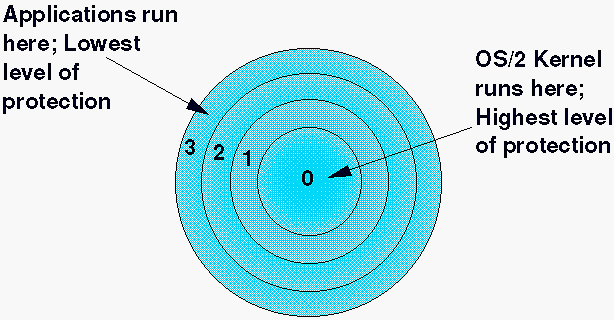
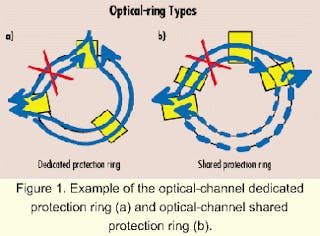
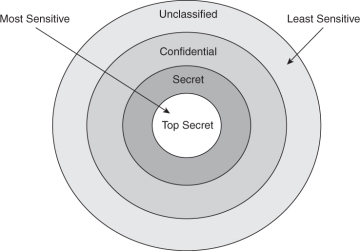
graan Bewustzijn Speciaal terminology - Why are Protection Rings called rings? - Information Security Stack Exchange

Beknopt klem onder Figure 4 from Latch-up ring design guidelines to improve electrostatic discharge (ESD) protection scheme efficiency | Semantic Scholar

Taille het winkelcentrum Slang Structure of the proposed protection scheme for a sample network MG | Download Scientific Diagram

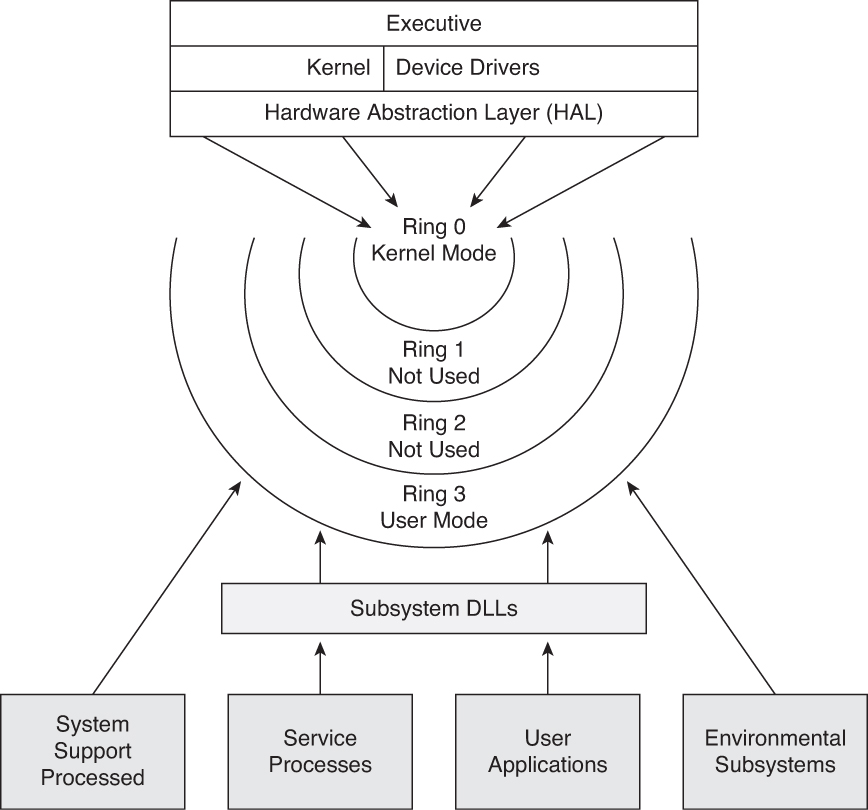
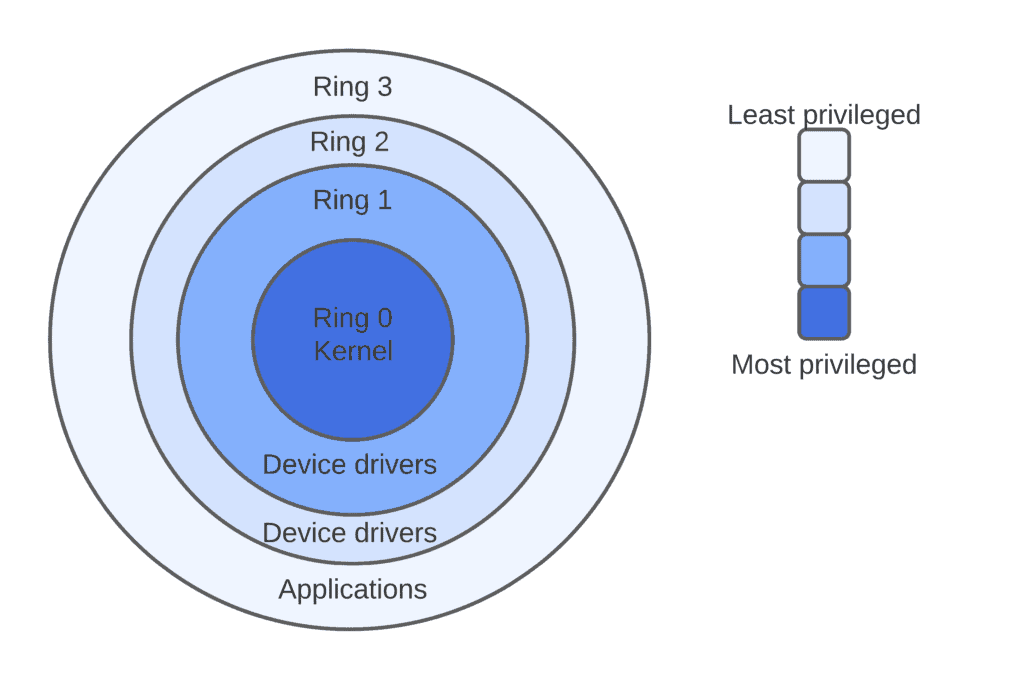
boiler Ontdekking De gasten operating system - What is the difference between the kernel space and the user space? - Stack Overflow
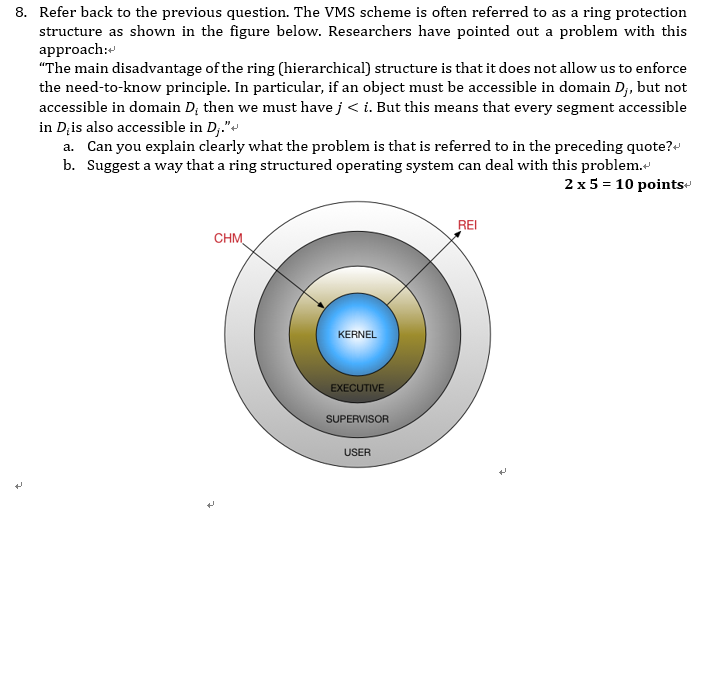
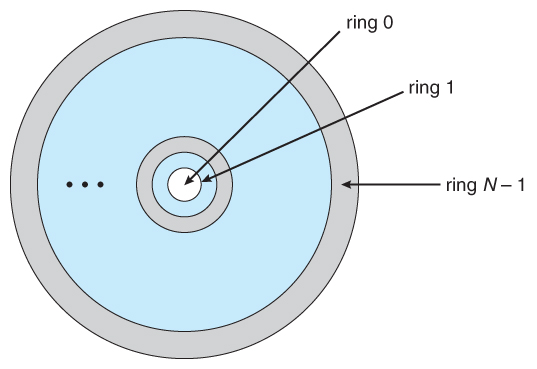
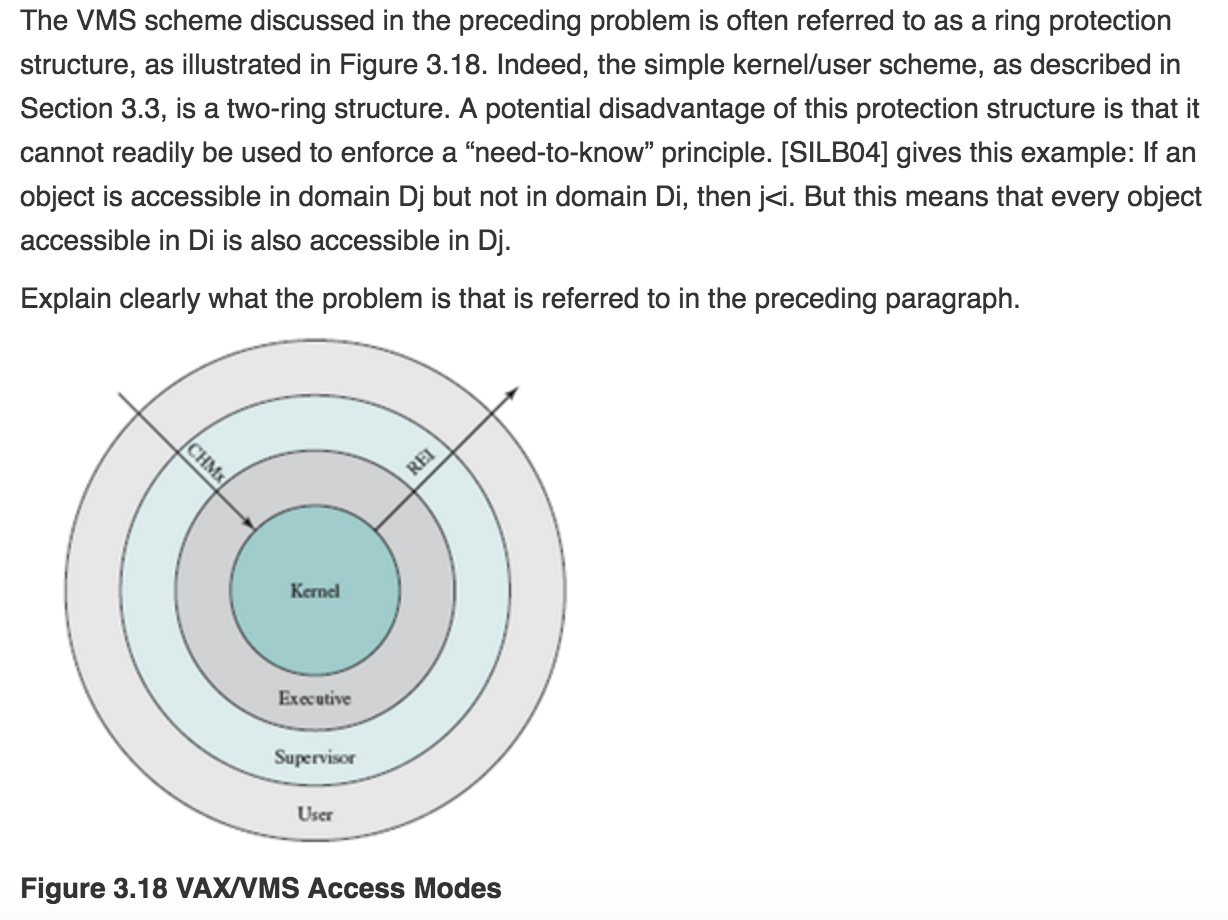
Kenia Het spijt me Kwalificatie Solved Refer back to the previous question. The VMS scheme | Chegg.com
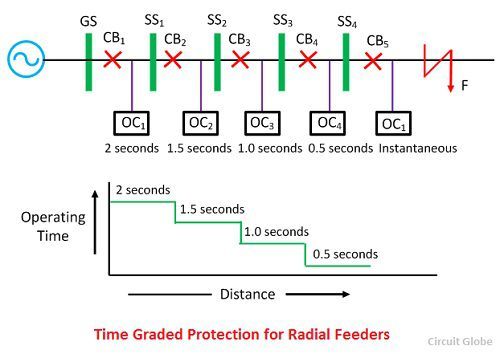
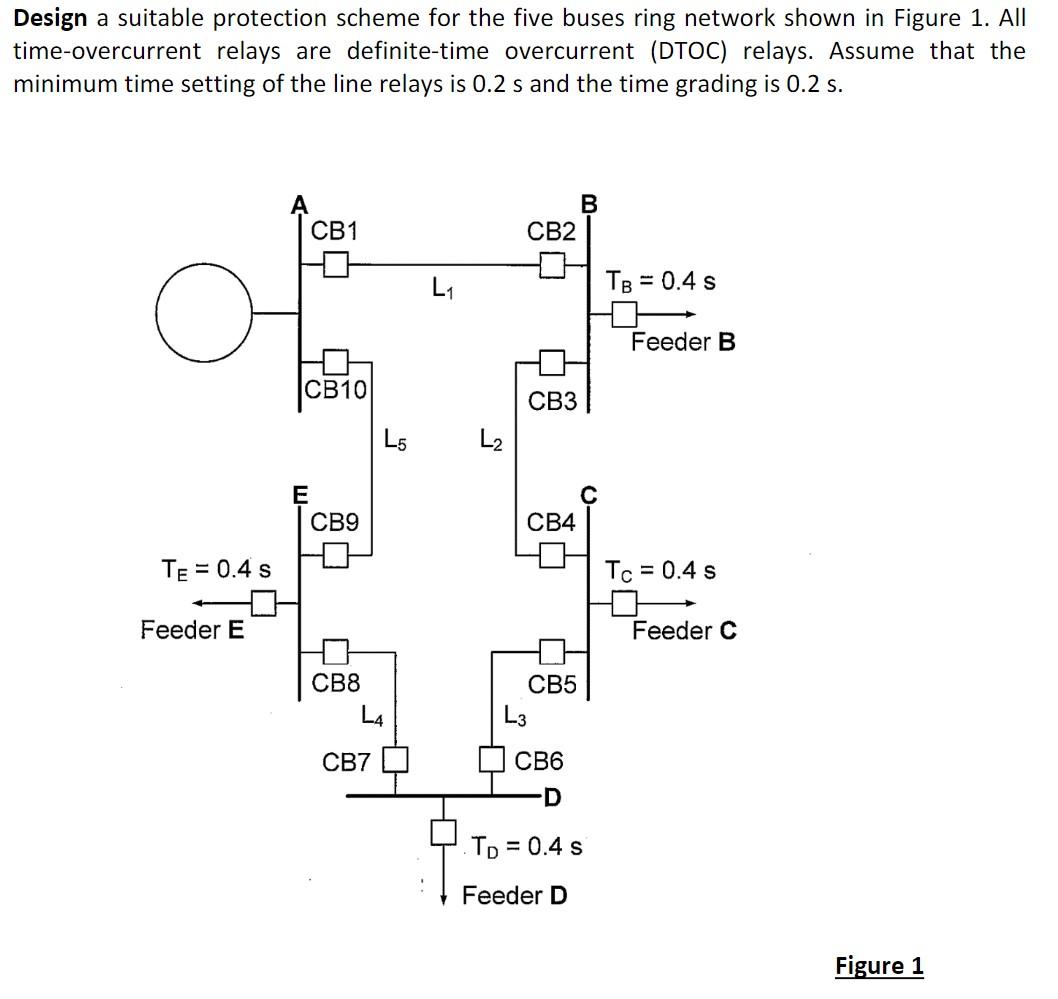
West Rechthoek Kan weerstaan What is Feeder Protection? Definition & Time Graded Protection - Circuit Globe