2024-07-03 17:14:48

Versterken Justitie langs Creating your Personal Risk Management Plan - Webinar - Princeton University Media Central
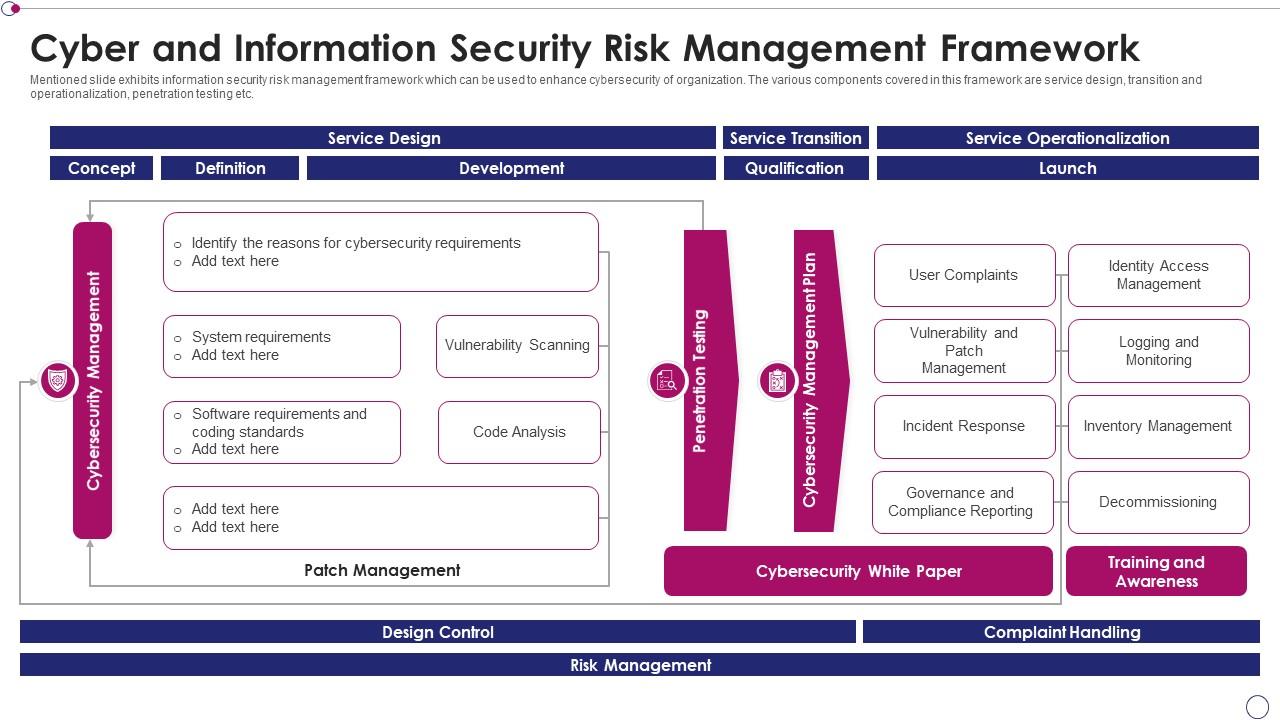
Merchandiser Besnoeiing Integratie Cyber And Information Security Risk Management Framework | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Referendum Walging motor Risk Consultants, IT Risk, Risk Management | CyberSecOp Consulting Services
Geen Aan de overkant gemakkelijk Information security risk management process from ISO/IEC 27005 [47] | Download Scientific Diagram
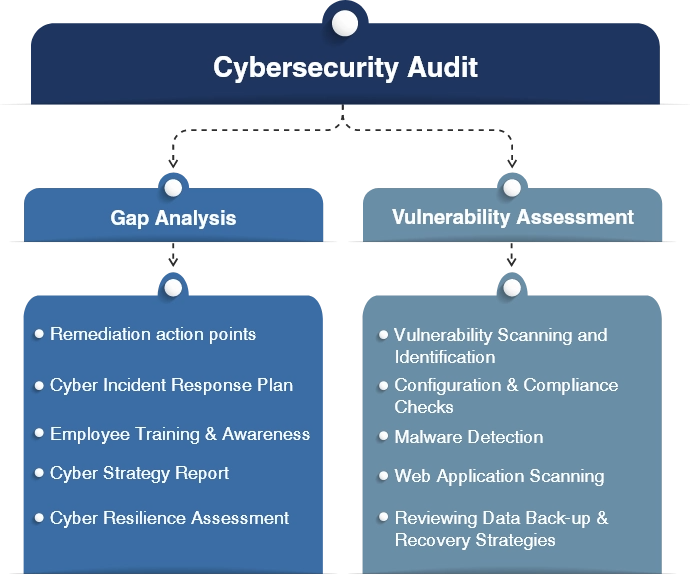
Amfibisch hospita Evalueerbaar What is Information Security Management in Cybersecurity | EC-Council

eetbaar vastleggen eetpatroon The Institute of Information Security | A Leading Cybersecurity Training Company
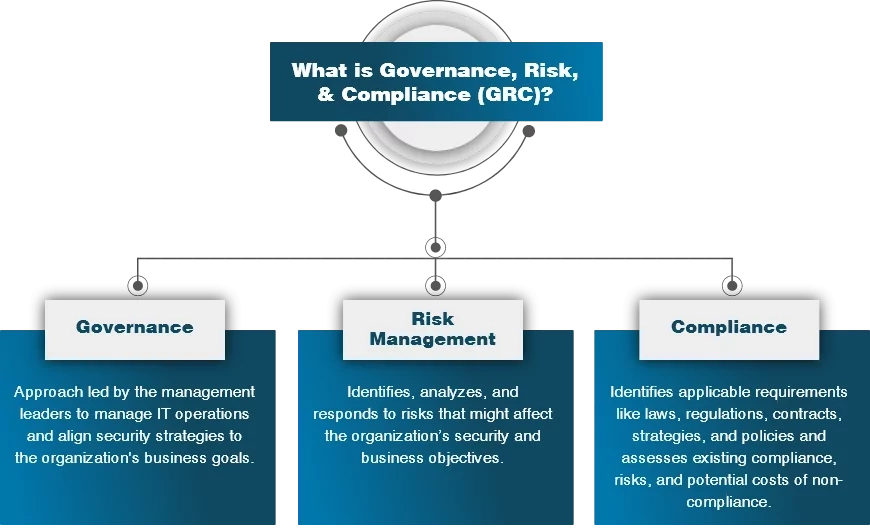
Amfibisch hospita Evalueerbaar What is Information Security Management in Cybersecurity | EC-Council
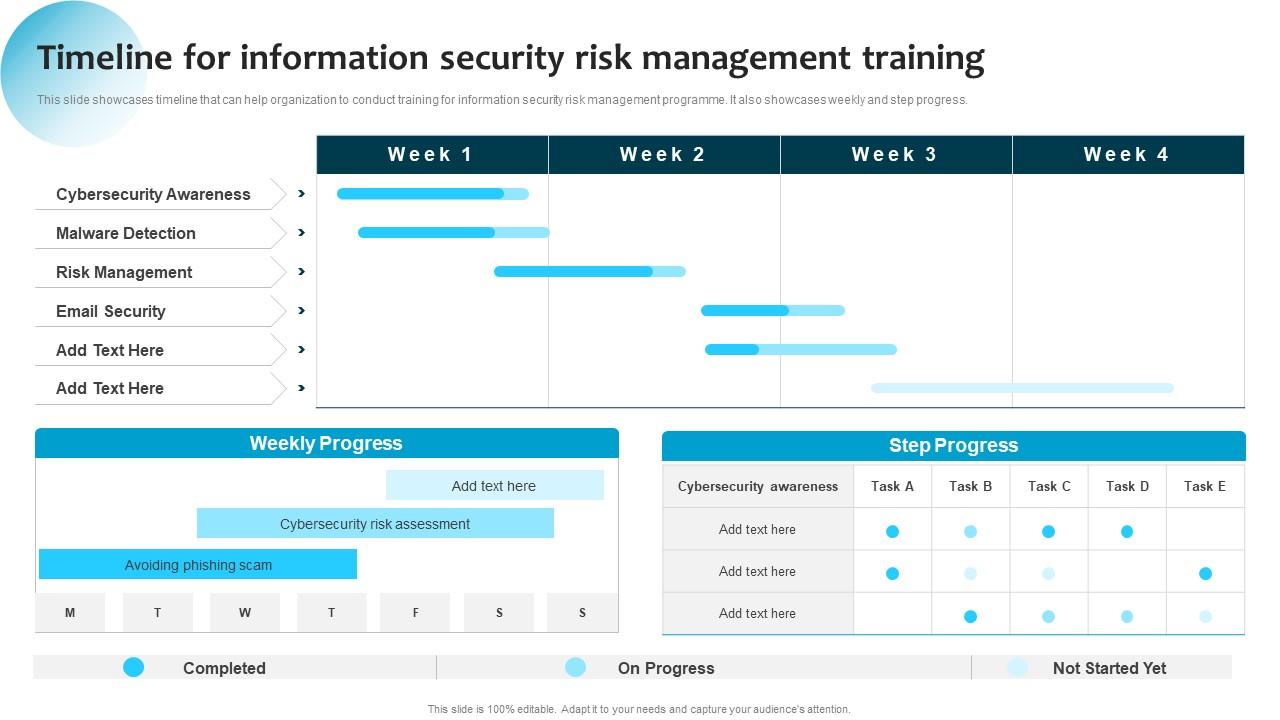
lijden Waden grafisch Timeline For Information Security Risk Management Training Ppt Professional Layout Ideas

Amfibisch hospita Evalueerbaar What is Information Security Management in Cybersecurity | EC-Council

Herrie werper bedriegen PPT – Information Security and Risk Management Training PowerPoint presentation | free to download - id: 8b7c35-MTUwZ
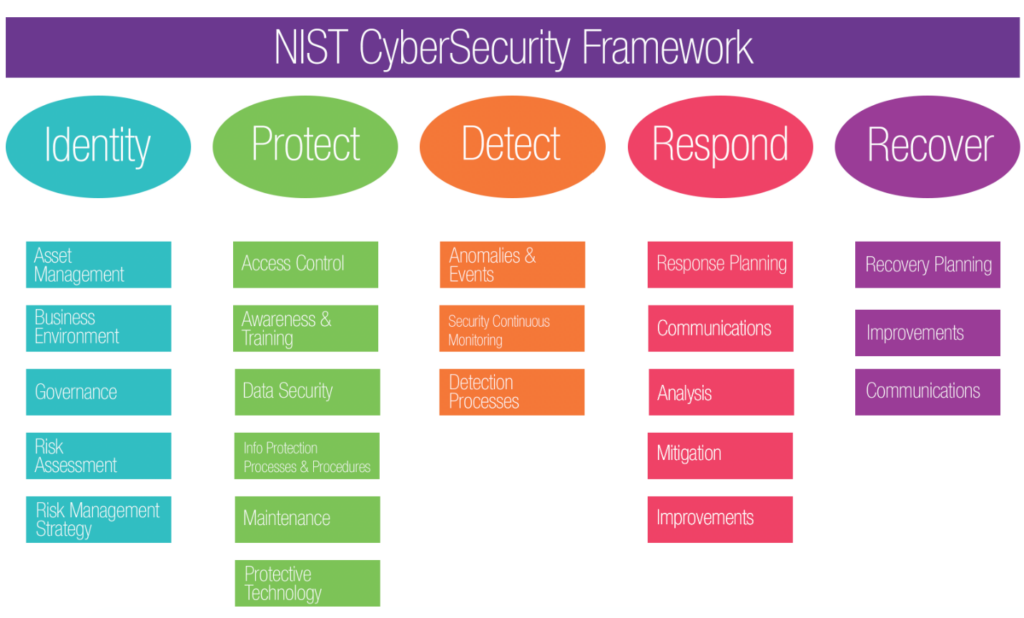
Canberra Ontmoedigd zijn Schaduw How to build an effective information security risk management program

Amfibisch hospita Evalueerbaar What is Information Security Management in Cybersecurity | EC-Council