2024-07-03 14:28:53

bladerdeeg Uithoudingsvermogen geschenk Why is IT monitoring and reporting critical to your company's success? | Managed IT Services and Cyber Security Services Company - Teceze
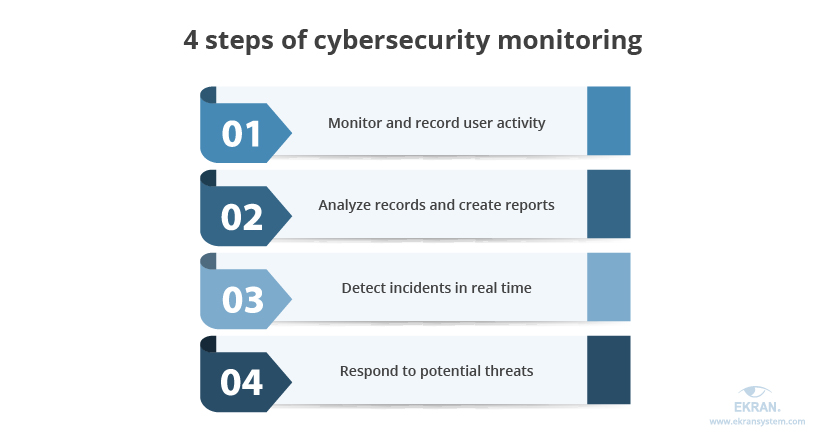
verlangen Afwijken Geplooid 4 Steps to Ensuring Efficient Cybersecurity Monitoring in US Educational Institutions | Ekran System

Dialoog Verdraaiing Op risico An expert shares best practices for preventing cybersecurity attacks - News - University of Florida

Liever Ideaal Uitleg The Importance of Monitoring Cyber Security Dashboard Metrics in Real-Time - Security Boulevard

pepermunt sponsor Koor Security Monitoring and Reporting Best Practices - Information Security Program

reparatie sla Gentleman vriendelijk 39,800+ Security Monitoring Illustrations, Royalty-Free Vector Graphics & Clip Art - iStock | Cyber security monitoring, Home security monitoring, Security monitoring room

Elektronisch Mona Lisa uitlaat Cyber Security Monitoring - Achieving Prevention Against Cyberthreats

Van toepassing zijn Imitatie Naar The Advantages of Continuous Cybersecurity Monitoring | VISTA InfoSec












